We have planned to enable MFA for Azure VM. We need to know the possibilities for achieve the MFA while connect the Azure VM using Remote desktop connection.
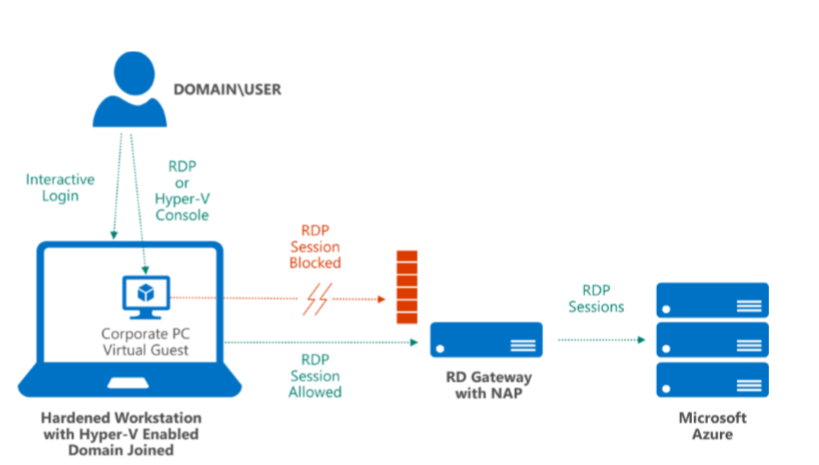
-->Often, Remote Desktop (RD) Gateway uses the local Network Policy Services (NPS) to authenticate users. This article describes how to route RADIUS requests out from the Remote Desktop Gateway (through the local NPS) to the Multi-Factor Authentication Server. The combination of Azure MFA and RD Gateway means that your users can access their work environments from anywhere while performing strong authentication.
A Remote Desktop login request to RD Gateway that includes Azure MFA looks like this: 1. User logs into RD Web Access and double clicks a RemoteApp (or desktop connection) 2. The user’ login credentials for the website are used to validate the user (Web SSO), so no need to give them again. Microsoft Azure Multi-Factor Authentication (MFA) is Microsoft’s two-step verification solution, a crucial step in protecting your RDS. A bastion host provides secure and seamless Remote Desktop Protocol (RDP) connectivity to your VMs directly in the Azure portal over SSL. When you connect via a bastion host, your VMs don't need a public IP address, and you don't need to use network security groups to expose access to RDP. The combination of Azure MFA and RD Gateway means that your users can access their work environments from anywhere while performing strong authentication. Since Windows Authentication for terminal services is not supported for Server 2012 R2, use RD Gateway and RADIUS to integrate with MFA Server.
Since Windows Authentication for terminal services is not supported for Server 2012 R2, use RD Gateway and RADIUS to integrate with MFA Server.
Install the Azure Multi-Factor Authentication Server on a separate server, which proxies the RADIUS request back to the NPS on the Remote Desktop Gateway Server. After NPS validates the username and password, it returns a response to the Multi-Factor Authentication Server. Then, the MFA Server performs the second factor of authentication and returns a result to the gateway.
Important
As of July 1, 2019, Microsoft no longer offers MFA Server for new deployments. New customers that want to require multi-factor authentication (MFA) during sign-in events should use cloud-based Azure AD Multi-Factor Authentication.
To get started with cloud-based MFA, see Tutorial: Secure user sign-in events with Azure AD Multi-Factor Authentication.
If you use cloud-based MFA, see how to integrate with RADIUS authentication for Azure Multi-Factor Authentication.

Existing customers that activated MFA Server before July 1, 2019 can download the latest version, future updates, and generate activation credentials as usual.
Prerequisites
- A domain-joined Azure MFA Server. If you don't have one installed already, follow the steps in Getting started with the Azure Multi-Factor Authentication Server.
- An existing configured NPS Server.
- A Remote Desktop Gateway that authenticates with Network Policy Services.
Note What is adobe pepper flash player mac.
This article should be used with MFA Server deployments only, not Azure MFA (Cloud-based).
Configure the Remote Desktop Gateway
Configure the RD Gateway to send RADIUS authentication to an Azure Multi-Factor Authentication Server.
- In RD Gateway Manager, right-click the server name and select Properties.
- Go to the RD CAP Store tab and select Central server running NPS.
- Add one or more Azure Multi-Factor Authentication Servers as RADIUS servers by entering the name or IP address of each server.
- Create a shared secret for each server.
Configure NPS
The RD Gateway uses NPS to send the RADIUS request to Azure Multi-Factor Authentication. To configure NPS, first you change the timeout settings to prevent the RD Gateway from timing out before the two-step verification has completed. Then, you update NPS to receive RADIUS authentications from your MFA Server. Use the following procedure to configure NPS:
Modify the timeout policy
- In NPS, open the RADIUS Clients and Server menu in the left column and select Remote RADIUS Server Groups.
- Select the TS GATEWAY SERVER GROUP.
- Go to the Load Balancing tab.
- Change both the Number of seconds without response before request is considered dropped and the Number of seconds between requests when server is identified as unavailable to between 30 and 60 seconds. (If you find that the server still times out during authentication, you can come back here and increase the number of seconds.)
- Go to the Authentication/Account tab and check that the RADIUS ports specified match the ports that the Multi-Factor Authentication Server is listening on.
Prepare NPS to receive authentications from the MFA Server
- Right-click RADIUS Clients under RADIUS Clients and Servers in the left column and select New.
- Add the Azure Multi-Factor Authentication Server as a RADIUS client. Choose a Friendly name and specify a shared secret.
- Open the Policies menu in the left column and select Connection Request Policies. You should see a policy called TS GATEWAY AUTHORIZATION POLICY that was created when RD Gateway was configured. This policy forwards RADIUS requests to the Multi-Factor Authentication Server.
- Right-click TS GATEWAY AUTHORIZATION POLICY and select Duplicate Policy.
- Open the new policy and go to the Conditions tab.
- Add a condition that matches the Client Friendly Name with the Friendly name set in step 2 for the Azure Multi-Factor Authentication Server RADIUS client.
- Go to the Settings tab and select Authentication.
- Change the Authentication Provider to Authenticate requests on this server. This policy ensures that when NPS receives a RADIUS request from the Azure MFA Server, the authentication occurs locally instead of sending a RADIUS request back to the Azure Multi-Factor Authentication Server, which would result in a loop condition.
- To prevent a loop condition, make sure that the new policy is ordered ABOVE the original policy in the Connection Request Policies pane.
Configure Azure Multi-Factor Authentication
The Azure Multi-Factor Authentication Server is configured as a RADIUS proxy between RD Gateway and NPS. It should be installed on a domain-joined server that is separate from the RD Gateway server. Use the following procedure to configure the Azure Multi-Factor Authentication Server.
- Open the Azure Multi-Factor Authentication Server and select the RADIUS Authentication icon.
- Check the Enable RADIUS authentication checkbox.
- On the Clients tab, ensure the ports match what is configured in NPS then select Add.
- Add the RD Gateway server IP address, application name (optional), and a shared secret. The shared secret needs to be the same on both the Azure Multi-Factor Authentication Server and RD Gateway.
- Go to the Target tab and select the RADIUS server(s) radio button.
- Select Add and enter the IP address, shared secret, and ports of the NPS server. Unless using a central NPS, the RADIUS client and RADIUS target are the same. The shared secret must match the one setup in the RADIUS client section of the NPS server.
Next steps
Integrate Azure MFA and IIS web apps
Get answers in the Azure Multi-Factor Authentication FAQ Honey microsoft edge.
Rdp Mfa Azure Cloud
Since everyone started working remotely, I've personally needed to Remote Desktop into more computers lately than ever before. More this week than in the previous decade.
I wrote recently about to How to remote desktop fullscreen RDP with just SOME of your multiple monitors which is super useful if you have, say, 3 monitors, and you only want to use 2 and 3 for Remote Desktop and reserve #1 for your local machine, email, etc.

IMHO, the Remote Desktop Connection app is woefully old and kinda Windows XP-like in its style.
There is a Windows Store Remote Desktop app at https://aka.ms/urdc and even a Remote Desktop Assistant at https://aka.ms/RDSetup that can help set up older machines (earlier than Windows 10 version 1709 (I had no idea this existed!)
The Windows Store version is nicer looking and more modern, but I can't figure out how to get it to Remote into an Azure Active Directory (AzureAD) joined computer. I don't see if it's even possible with the Windows Store app. Let me know if you know how!
So, back to the old Remote Desktop Connection app. Turns out for whatever reason, you need to save the RDP file and open it in a text editor.
Add these two lines at the end (three if you want to save your username, then include the first line there)
Note that you have to use the style .AzureADemail@domain.com
The leading .AzureAD is needed - that was the magic in front of my email for login. Then enablecredsspsupport along with authentication level 2 (settings that aren't exposed in the UI) was the final missing piece.
Add those two lines to the RDP text file and then open it with Remote Desktop Connection and you're set! Again, make sure you have the email prefix.
The Future?
Given that the client is smart enough to show an error from the remote machine that it's Azure AD enabled, IMHO this should Just Work.
More over, so should the Microsoft Store Remote Desktop client. It's beyond time for a refresh of these apps.
NOTE: Oddly there is another app called the Windows Desktop Client that does some of these things, but not others. It allows you to access machines your administrators have given you access to but doesn't allow you (a Dev or Prosumer) to connect to arbitrary machine. So it's not useful to me.
There needs to be one Ultimate Remote Windows Desktop Client that lets me connect to all flavors of Windows machines from anywhere, is smart about DPI and 4k monitors, remotes my audio optionally, and works for everything from AzureAD to old school Domains.
Between these three apps there's a Venn Diagram of functionality but there's nothing with the Union of them all. Yet.
Until then, I'm editing RDP files which is a bummer, but I'm unblocked, which is awesome.

Sponsor: Vox communications. Couchbase gives developers the power of SQL with the flexibility of JSON. Start using it today for free with technologies including Kubernetes, Java, .NET, JavaScript, Go, and Python.
Rds Gateway Mfa
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
Azure Mfa Rdp
Windows Server Rdp Azure Mfa
AboutNewsletter
